PhishSleuth
.
With the increasing number of crime the crime detection tools has also increased at an alarming rate. On the 3rd of March, the economic times of India mentioned that:- About 30 crore people are vulnerable to phishing attacks in India, of which 5 lakh potentially fall prey to scamsters. That's why we came up with the idea of PhishSleuth.It is a Phishing Links Detection and Alert system is to help individuals and organizations protect themselves from phising attacks. Phishing attacks are a common and growing threat to personal and business security, and they can result in the loss of sensitive information, financial loss, and other consequences. BY developing a solution that can detect and alert users of potential phishing attacks across vsrious digital channels, we can provide an additional layer of security and protection attacks across various digital channels, we can provide an additional layer of security and protection. Ultimately, the goal of developing a solution like this is to empower individuals and organixations to protect themselves from phishing attacks and minimize the risk of data breaches, financial loss, and other negative consequences.

This technique is the most common, and often occurs when cybercriminals send emails with phishing URLs to try and obtain
sensitive user information. According to a Forcepoint article, “an email may present with links that spoof legitimate URLs;
manipulated links may feature subtle misspellings or use of a subdomain.” Once access is granted through these links,
cybercriminals are able to successfully launch an attack.

Cybercriminals employ a deceitful tactic of sending customized text messages with the aim of duping unsuspecting individuals into revealing their personal data. The scheme involves incorporating a malevolent hyperlink, which reroutes users to a fake website intended for phishing, and subsequently exposing their confidential information to the perpetrator.

URL phishing is a type of cyber attack where an attacker creates a fake website that looks similar to a legitimate one in order to trick users into entering their sensitive information, such as login credentials, credit card numbers, and other personal data. The attacker typically uses social engineering techniques to lure the victim into clicking on a malicious link that leads to the fake website. Once the user enters their information on the fake website, the attacker can use it for fraudulent purposes, such as identity theft, financial fraud, or other malicious activities.

Support Vector Machine
This tec is a popular supervised learning algorithm used for classification and regression analysis. The main idea behind SVM is to find a hyperplane (a line in two dimensions,
a plane in three dimensions, etc.) that separates the data points into different classes while maximizing the margin between the hyperplane and the closest points of each class.

Decision Tree
A Decision Tree is a popular machine learning algorithm used for both classification and regression problems. It is a simple yet powerful model that can be easily understood and interpreted by humans.
A decision tree consists of nodes, branches, and leaves. Each internal node represents a test on a particular feature, and each branch represents the outcome of that test. The leaves represent the final decision or prediction.
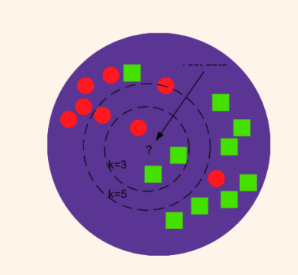
K-Nearest Neighbour
Anchor
This a simple and effective algorithm used for classification and regression tasks. In the case of classification, the KNN algorithm assigns an unknown sample to the class that is most common among its k nearest neighbors in the training data.
In the case of regression, the KNN algorithm assigns an unknown sample the average of its k nearest neighbors.

Rotation Forest
This Technology is an ensemble method that combines the idea of feature extraction with the traditional ensemble methods. RoF creates multiple random feature subsets and applies a principal component analysis (PCA) rotation to each subset to generate a new set of uncorrelated features. Then, it trains a base classifier on each rotated feature subset and aggregates the predictions of all the base classifiers to make the final prediction.
Takes few seconds to detect spam
data preprocessing
Using Python, AI, Random forest
Using HTML, CSS, JavaScript
Using Python and Flask
SVM, Decision Tree
Jalandhar, IN
+91-8600322935
syntaxterminators@gmail.com